We are pleased to announce that the new IAP website, designed and developed by Mint, has just launched. (July 2024). Wellis Technology provided the custom PHP backend screens and facilities, that allow members to view and update their details and register for IAP webinars.
The IAP are a respected and established professional body and charity. They have members in over 30 countries and liaise with government, academia and employers. Their objective is to ‘Improve Software for Society’.
The IAP took advantage of Mint Designs Mint Mojo service and over the last 18 months they have been working on a brand refresh, created a brand guidelines document and promotional materials. The main objective of the commission was to create a new website which replaced a dated, word-heavy site with poor user experience.
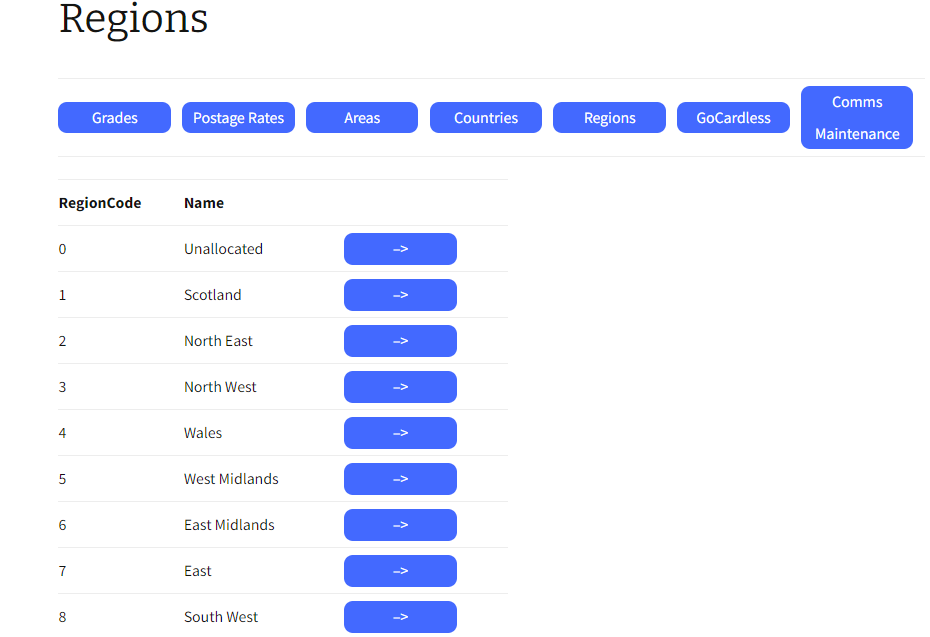
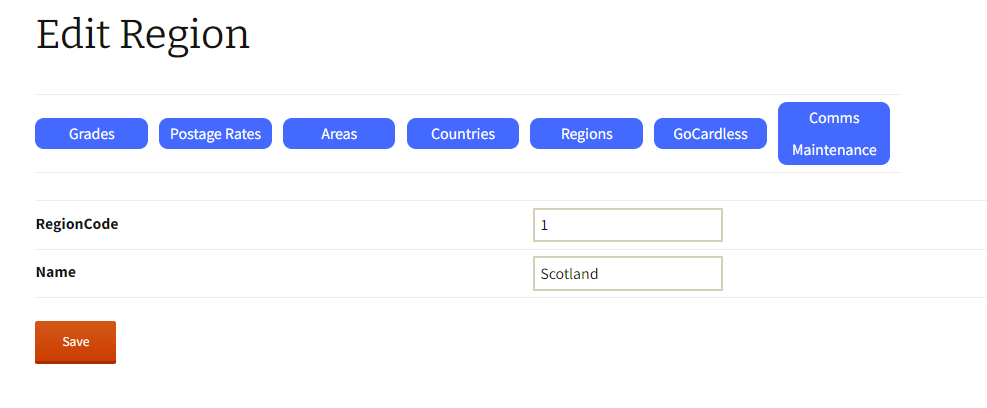
Wellis Technology, have written a series of backend PHP scripts to allow members to review and amend their data, look up and pay their subscriptions, print reciepts. In addition, the ability to reserve a spot at the Institutions webinars, which are on a wide range of software development issues from Cyber Security to AI. We were responsible for the integration of Mint Designs new site and the existing infrastructure and backend systems.
Working with Kate Honey at Mint Design to deliver this amazing site has been a real pleasure as our unique skillsets coming together. The new site that will serve the IAP well moving into the future; it’s contemporary, well-written and has a broad appeal. Hope you agree: www.iap.org.uk, and if you work in the software development sector you may want to look into joining the IAP!






 Recently one of my clients asked me about a possible upgrade on his PC.
Recently one of my clients asked me about a possible upgrade on his PC.